Permissions
Permissions can be enforced on resources and data in Onehouse with roles and privileges.
Onehouse Resources and Data Objects
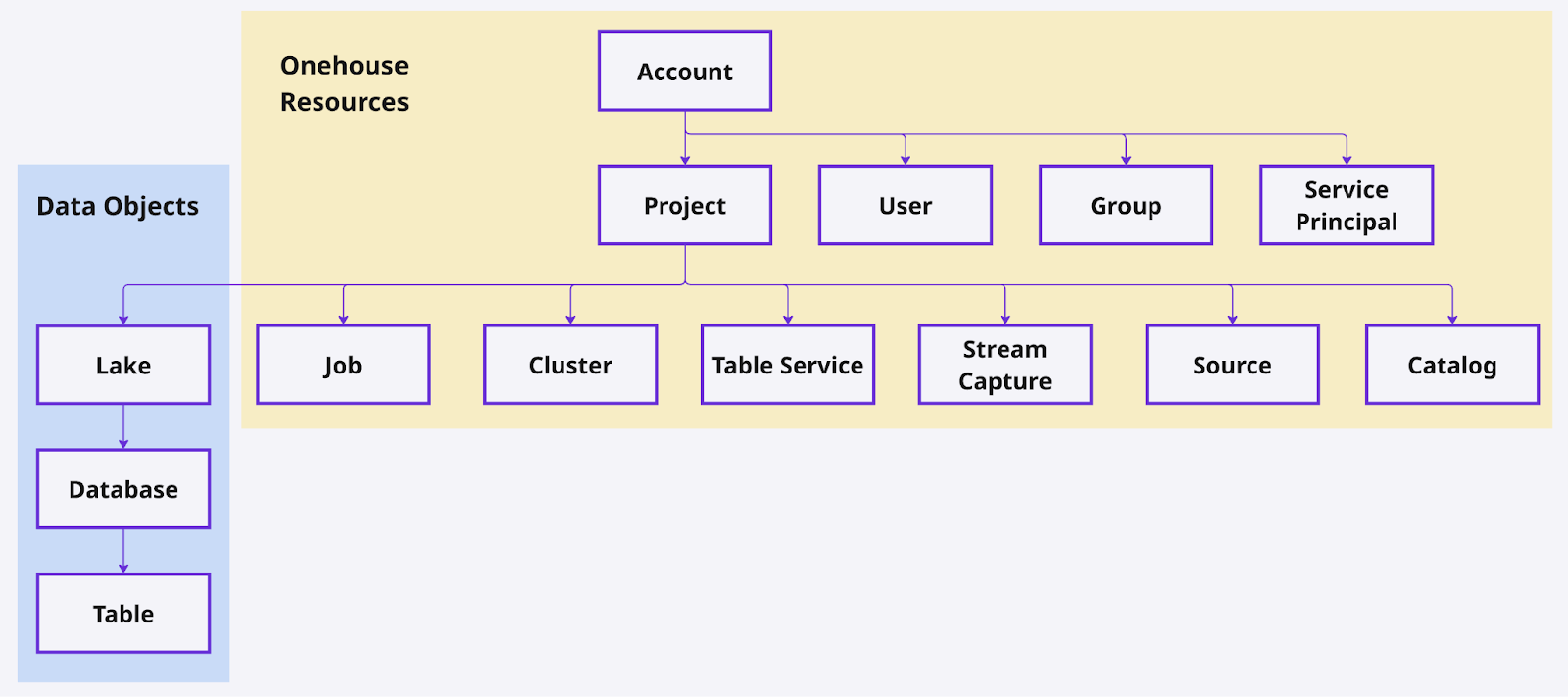
Permissions can be set on the following entities:
| Entity | Description | Permission Type | Examples |
|---|---|---|---|
| Onehouse Resources | Logical Onehouse entities in your account or project. | Roles | Account, Projects, Users, Groups, Service Principals, Jobs, Clusters, Table Services, Stream Captures, Sources, and Catalogs |
| Data Objects | Your data stored and/or managed by Onehouse. | Privileges | Lakes, Databases, and Tables |
What permissions are required to create entities?
A user must meet the following prerequisites to create resources and objects in Onehouse:
| Entity | Prequisites for creation |
|---|---|
| Account | No account exists for the email domain |
| Project | Account Admin role |
| Group | Account Admin role |
| Service Principal | Account Admin role |
| User | Project Admin role |
| Stream Capture |
|
| Cluster | Project Admin role |
| Table Service | Data privileges on the table (see below) |
| Job | Cluster User role on the Cluster |
| Catalog | N/A (anyone in project can create) |
| Source | N/A (anyone in project can create) |
| Lake | Project Admin role |
| Database | Create Database privilege on the Lake |
| Table | Create Table privilege on the Database |
Roles for Onehouse Resources
Account
The following roles can be granted on a Onehouse Account:
- Member
- Admin
| Ability | Member | Admin |
|---|---|---|
| Modify account & billing settings | X | |
| Create projects | X | |
| Create groups | X | |
| Create service principals | X | |
| Configure SCIM identity sync | X |
Project
The following roles can be granted on a Project:
- Member
- Admin
| Ability | Member | Admin |
|---|---|---|
| View/Use/Edit/Manage entities with granted permissions | X | X |
| Open the project | X | X |
| View project integrations | X | X |
| View project usage | X | X |
| Create Sources | X | X |
| Create Catalogs | X | X |
| Create Jobs | X (with required permissions) | X |
| Create Table Services | X (with required permissions) | X |
| Create Stream Captures | X (with required permissions) | X |
| Create users | X | |
| Add users to the project | X | |
| Edit user permissions in the project | X | |
| Remove users | X | |
| Connect a cloud account | X | |
| Create Clusters | X | |
| Create Lakes | X | |
| Create and edit project integrations | X | |
| Create and delete API tokens | X | |
| Inherit all permissions for all entities in the project | X |
Group
The following roles can be granted on a Group:
- Member
- Manager
| Ability | Member | Manager |
|---|---|---|
| Create new groups | ||
| View metadata for group | X | X |
| Assign roles and privileges to group | X | |
| Remove roles and privileges from group | X | |
| Edit group members | X | |
| Edit group name | X | |
| Delete group | X |
Service Principal
The following roles can be granted on a Service Principal:
- User
- Manager
| Ability | User | Manager |
|---|---|---|
| Create new service principals | ||
| Assign roles and privileges to service principal | X | |
| Remove roles and privileges from service principal | X | |
| Edit service principal members | X | |
| Edit service principal name | X | |
| Delete service principal | X | |
| Create API tokens for the service principal | X |
Cluster
The following roles can be granted on a Cluster:
- Viewer
- User
- Editor
- Manager
| Ability | Viewer | User | Editor | Manager |
|---|---|---|---|---|
| View Cluster definition | X | X | X | X |
| Assign Stream Captures / Jobs to Cluster | X | X | X | |
| View Cluster endpoint | X | X | X | |
| Edit Cluster definition | X | X | ||
| Modify permissions | X | |||
| Delete Cluster | X |
Source (coming soon)
The following roles can be granted on a Source:
- Viewer
- User
- Editor
- Manager
| Ability | Viewer | User | Editor | Manager |
|---|---|---|---|---|
| View source definition | X | X | X | X |
| Use source in a Stream Capture | X | X | X | |
| Edit source definition | X | X | ||
| Modify permissions | X | |||
| Delete source | X |
Catalog (coming soon)
The following roles can be granted on a Catalog:
- Viewer
- User
- Editor
- Manager
| Ability | Viewer | User | Editor | Manager |
|---|---|---|---|---|
| View catalog definition | X | X | X | X |
| Use catalog in a Stream Capture | X | X | X | |
| Use catalog in a MetaSync | X | X | X | |
| Edit catalog definition | X | X | ||
| Modify permissions | X | |||
| Delete source | X |
Job (coming soon)
The following roles can be granted on a Job:
- Viewer
- User
- Editor
- Manager
| Ability | Viewer | User | Editor | Manager |
|---|---|---|---|---|
| View Job definition | X | X | X | X |
| View Job run metadata | X | X | X | X |
| View Job run driver logs and Spark UI | X | X | X | |
| Trigger Job run | X | X | X | |
| Cancel Job run | X | X | X | |
| Edit Job definition | X | X | ||
| Modify permissions | X | |||
| Delete Job | X |
Stream Capture (coming soon)
The following roles can be granted on a Stream Capture:
- Viewer
- Editor
- Manager
| Ability | Viewer | Editor | Manager |
|---|---|---|---|
| View Stream Capture definition | X | X | X |
| View driver logs | X | X | X |
| Edit Stream Capture definition | X | X | |
| Pause / Resume Stream Capture | X | X | |
| Clean & Restart Stream Capture | X | ||
| Delete Stream Capture | X | ||
| Modify permissions | X |
Table Service
Table Services do not have their own roles, and instead depend on the data privileges of the table itself. To create/edit/remove/pause/resume a Table Service, a user must:
- Have
Userrole on the table’s Services Cluster - Have the required data privileges on the table (see below)
To view the definition, metrics, and run history of a Table Service, a user must:
- Have the
DESCRIBEprivilege on the table
| Table Service | Create/Edit Requirement Privileges | View Definition & History Privileges |
|---|---|---|
| Compaction | ALTER | DESCRIBE |
| Clustering | ALTER | DESCRIBE |
| Cleaning | ALTER | DESCRIBE |
| MetaSync | SELECT | DESCRIBE |
Notification
Notifications are handled based on the roles for the underlying resources. Users can view and dismiss notifications for all resources the have access to view.
Data Privileges
The following privileges can be granted on Lakes, Databases, and/or Tables.
Privileges propogate down to their child objects (ie. lake privileges propogate to child databases; database privileges propogate to child tables).
Example: A User granted CREATE_TABLE privilege on a lake receives this privilege for all databases (current and future) in the lake, and the privilege is enforced on those databases.
How to read the table below:
- Grantable Scope is the Data Objects the privilege can be granted on.
- Enforced On refers to the Data Objects the privilege can be enforced on.
| Privilege | Grantable Scope | Enforced On | What You Can Do |
|---|---|---|---|
| ALL | Lake, Database, Table | Lake, Database, Table | All privileges on the object and its children |
| MANAGE | Lake, Database, Table | Lake, Database, Table | Grant and revoke privileges on the object and its children |
| DROP | Lake, Database, Table | Lake, Database, Table | Drop the object and its children |
| DESCRIBE | Lake, Database, Table | Lake, Database, Table | View object metadata only – no data access |
| CREATE_DATABASE | Lake | Lake | Create Databases in the Lake |
| CREATE_TABLE | Lake, Database | Database | Create Tables in the Database or Lake |
| ALTER | Lake, Database, Table | Table | Alter metadata (e.g., schema) and change the table's Services Cluster |
| SELECT | Lake, Database, Table | Table | Read Table data |
| INSERT | Lake, Database, Table | Table | Insert/update/read data and create/restore savepoints |
| DELETE | Lake, Database, Table | Table | Delete data |